Complete EndPoint Protection With Extensive Threat Hunting And Expanded Visibility
Analyze your Entire Environment from the Base-Event Level in Real-Time. You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system.
ENDPOINT DETECTION & RESPONSE
Endpoint Monitoring Benefits
Continuous real-time visibility of your endpoints with detection & response. Your IT team will be able to identify attacks with the accurate root-cause analysis for effective remediation intelligence.
- Actionable Intelligence for Endpoint Remediation
- Reporting to Reduce Total Number of Incidents
- Alerts to Quickly Find Solution to Incidents
- Lightweight Agent with Cloud Delivered Updates
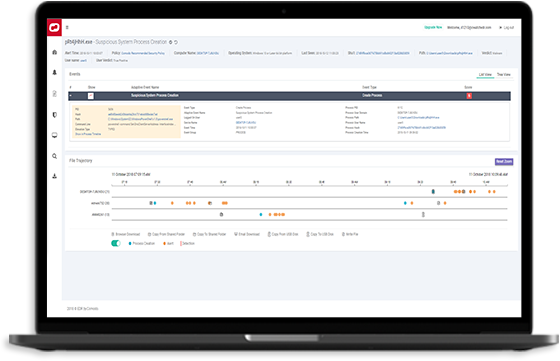
Enhance Your EPP To Prevent Ransomware, Data Breaches, & Malware
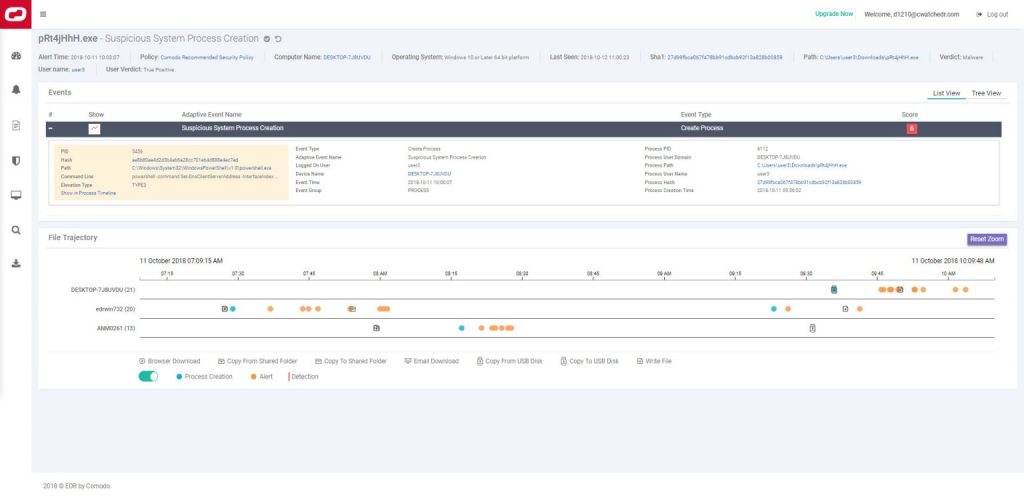 EDR FORECAST ANALYSIS
EDR FORECAST ANALYSISStay Ahead To Stop Cyber Attacks
- We will tailor the group policy to your requirements including endpoint-specific policies for enhanced security.
- No hardware needed! Automatically updates signatures and checks processes executed in your environment continuously.
- Enable our lightweight agent to start counter-actions to dramatically streamline follow-up efforts for your IT dept.
 SUSPICIOUS ACTIVITY VALIDATION
SUSPICIOUS ACTIVITY VALIDATIONTrack Infected Endpoints For IT To Patch
- Protection against zero-day web threats, without hindering employee productivity.
- Detect 100% of unknown fileless threats with Comodo's intelligent file analysis engine.
- Apply our recommended policy, created upon a meticulous examination of threat behavior analytics.
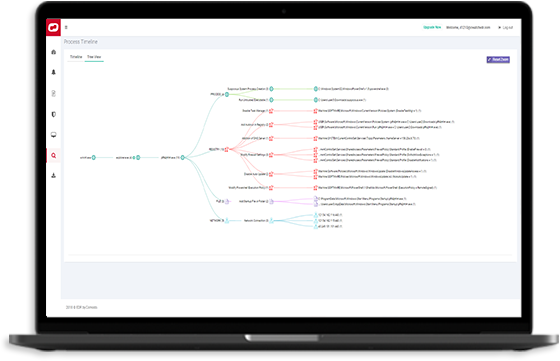 SEE THE CHAIN TO GET ACTIONABLE INTEL
SEE THE CHAIN TO GET ACTIONABLE INTELQuickly See How To Fix The Root Problems
- Attack vectors are shown on your dashboard streamlines any repairs by combining with file trajectory and process hierarchy.
- Process-based events are shown in a tree-view structure to help analysts better understand process behavior.
- Device trajectory details are provided with separate screens to drill down into devices for insight when investigating attack vectors.
WHY CHOOSE CYFYX
ENDPOINT DETECTION & RESPONSE
You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system.
Attack Chain Visualization
Early warning, detection and post-detection visualization
Intelligent File Analysis
Verdict 100% of unknown executables on all files
Granular Endpoint Detection
Tracks malicious processes taking place on your endpoints
SIEM Integration
Integrate with a SIEM to expand into more advanced security
Traffic Forwarding
Forward traffic using our intuitive agent
Fileless Threat Detecion
Detect 100% of unknown fileless threats
Recommended Security Policy
Apply our security policy based on threat behavior analytics
Cloud-Native Architecture
Signatures updated automatically without interruption
Real-Time Notifications
Set Email and SMS notifications to reduce reaction time
Expert Human Analysis
24 hr expert analysis of more sophisticated threats
ANALYST RECOGNITION
Our vendors have won consecutively across many verticals with their premier technology.
Innovation happens only when this type of dedication to cybersecurity reaches the many.
